IP Threat Intelligence Explained: A Vital Component in Cyber Defense Systems
In a world where digitalization has permeated every aspect of our lives, the term ‘cyber threat’ no longer rings the bells of obscure IT departments buried in basement offices. Instead, it is a mainstream concern, looming over businesses and individuals alike, waiting to exploit the digital footprint we all leave behind. IP Threat Intelligence emerges as the unsung hero, arming cybersecurity teams with the knowledge they need to combat these pervasive digital enemies.

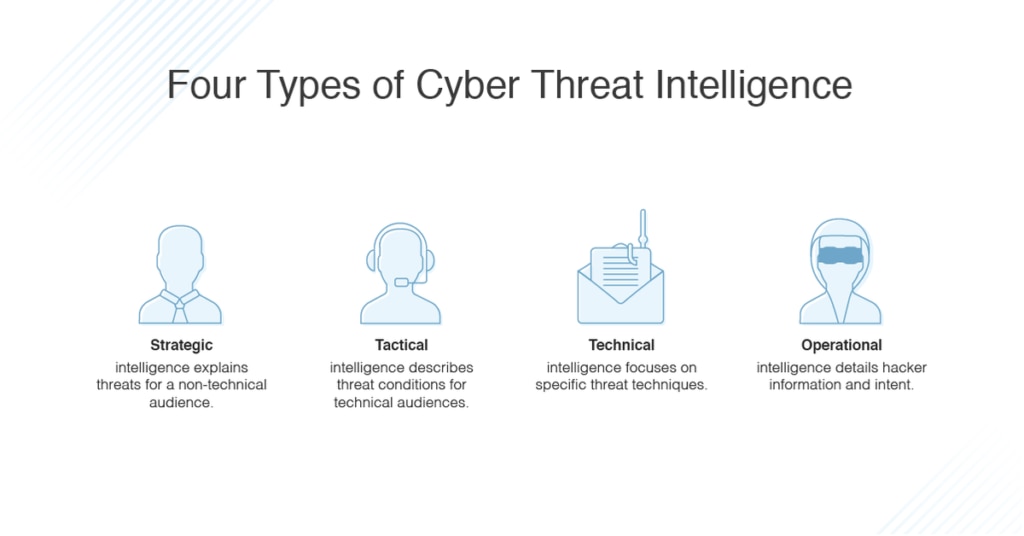
Understanding IP Threat Intelligence
Imagine your organization’s digital infrastructure is a castle. Beyond the moat, the perimeter walls, and the sturdy gates, a silent threat lurks. This invisible enemy does not march with armies; it infiltrates silently, through the ports and walls of a domain you thought impenetrable. IP Threat Intelligence is your guard on the watchtower, anticipating the enemy’s moves, understanding their tactics, and ready to sound the alarms.
IP Threat Intelligence is the knowledge gathered about potential cyber threats to an IP address or a collection of IP addresses. It’s a proactive approach to network security that employs real-time threat data to fend off potential attacks. At its core, IP Threat Intelligence aims to enhance situational awareness and help organizations make informed decisions when it comes to their cybersecurity posture.
The Necessity of IP Threat Intelligence
In a digital landscape teeming with IP-enabled devices, from smartphones to the Internet of Things (IoT), the sheer volume of potential attack vectors is staggering. IP Threat Intelligence is not only for tech giants with vast resources; it’s equally critical for small businesses that one might assume are too ‘under-the-radar’ to attract malicious intent. Without this intelligence, organizations face a stark reality – their information, from the mundane to the mission-critical, is perpetually at risk.
IP Threat Intelligence is the great equalizer in cybersecurity, providing businesses with the means to identify, categorize, and prioritize threats based on their potential impact. It is no longer a luxury but a necessity, particularly in the face of increasingly sophisticated cybercrime tactics.
How IP Threat Intelligence Works
At its most fundamental level, IP Threat Intelligence involves gathering data from various sources to identify malicious activities directed at a specific IP address. This may include scanning activity, malware distribution, or attempts to exploit vulnerabilities. Once collected, this data is analyzed to determine the nature and severity of the threat.
Data Collection: The intelligence process begins with robust data collection, often from various public and commercial sources. This ranges from monitoring forums and chat rooms where cyber criminals congregate to network activity logs and sensor data.
Data Analysis: The collected data is then cross-referenced and analyzed to identify patterns and attributes of malicious actors and their methods. This may involve the use of machine learning algorithms to process the vast amounts of information gathered.
Application: After analysis, the actionable insights derived from the intelligence are put into practice. This can take many forms, including blocking specific IP addresses, deploying additional security measures, or informing the development of more robust cybersecurity strategies.
Real-World Applications of IP Threat Intelligence
The efficacy of IP Threat Intelligence is evident in its real-world applications. Financial institutions have used it to stave off fraudulent activity, while governmental agencies employ it to protect sensitive information. Tech companies use it to safeguard intellectual property and maintain the integrity of their platforms.
In one case, a multinational corporation utilized IP Threat Intelligence to identify a pattern of unauthorized access to their proprietary databases, leading to the apprehension of the culprits before any critical data was compromised.
Selecting the Right IP Threat Intelligence Solution
The effectiveness of an IP Threat Intelligence solution hinges on several factors:
Accuracy and Timeliness: The intelligence must be both accurate and timely, providing organizations with the most current information to make decisions that can prevent attacks.
Scalability: The solution must be scalable, able to grow alongside an organization’s needs as their digital footprint expands.
Integration: A good IP Threat Intelligence solution should seamlessly integrate with an organization’s existing security infrastructure, enhancing its overall effectiveness.
Cost: While cost is a consideration, it’s important to view IP Threat Intelligence as an investment in long-term security rather than a mere expense.
By carefully considering these factors, organizations can select an IP Threat Intelligence solution that suits their specific needs and budget.
The Future of IP Threat Intelligence
The future of IP Threat Intelligence is a realm where automation and AI play a more significant role, not only in the analysis but also in the response to threats. We can expect to see more sophisticated tools that not only detect threats but also adapt and learn from them, creating a more robust and proactive defense mechanism.
Another trend on the horizon is the increased collaboration among businesses and security vendors, sharing threat data to create a more comprehensive view of the cybersecurity landscape.
Conclusion and Call to Action
The importance of IP Threat Intelligence cannot be understated. It is the beacon that illuminates the dark corners of the internet where threats reside. For organizations looking to fortify their cyber defenses in an increasingly digital world, investing in IP Threat Intelligence is investing in their future.
To those who may still view cybersecurity as an afterthought, it is a call to action. The cyber threat landscape is evolving at an unprecedented pace, demanding a proactive and informed approach to defense. Now is the time to take action, arm your defenses with IP Threat Intelligence, and safeguard what’s most important – your digital domain.